Posts Tagged ‘Facebook’
Unlike: Why Facebook's Like Button Sucks
Facebook’s new Like function makes me work harder to like something and that’s not what they were going for.
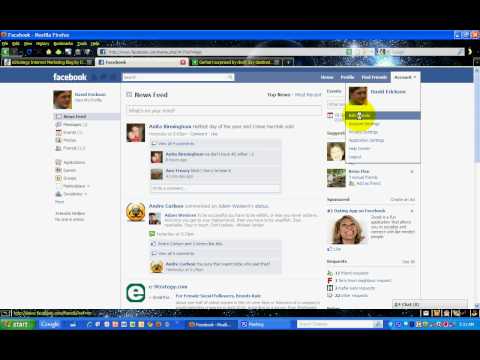
Read MoreTargeted Facebook Status Updates
In this screencast, David Erickson demonstrates how to target your Facebook status updates to only those Facebook Friends who are most likely to find a particular update of value.
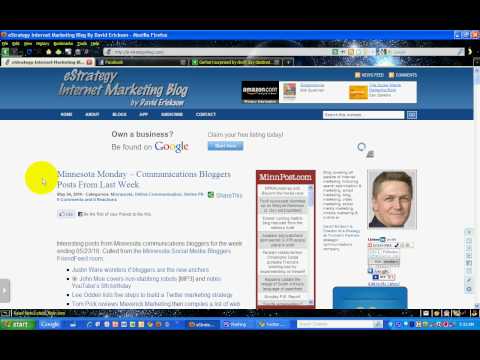
Read MoreCreating Facebook Lists
David Erickson demonstrates how to create Lists in Facebook in this screencast from the e-Strategy Internet Marketing Blog.
Read MoreSubscribe To Your Scoop
Watch a screencast of Izzy’s Ice Cream’s new RFID-enabled “Subscribe to your Scoop” ice cream flavor update customer service solution.
Read MoreScreencast: Facebook Like: Launch Partner Search Benefits
In this screencast, David Erickson look at the search benefits that Facebook Like launch partners such as ESPN and the Internet Movie Database get for their relationship with the social network.
Read MoreTom Scheck Discusses The Impact Of Social Media On Journalism
Minnesota Public Radio’s Tom Scheck talks about how journalism is changing at The Other Future of News event in December, 2009.
Read MoreBeyond Web Analytics
This presentation was given by Kristin Gast and David Erickson of Tunheim Partners on March 25, 2010, at the Minnesota Council of Nonprofits’ Technology and Communications Conference, Remix, Refresh, Reload: Balancing New Media & Traditional Strategy.
Read MorePunch Pizza's Social Media Use Featured
KARE 11 TV’s report on client Punch Pizza’s use of Facebook, Twitter and Flickr.
Read MoreMillennials Talk About Social Media Withdrawl
High school seniors George and James report back on their social networking furloughs (both tried to avoid social media for at least a week) and sum up the lessons they learned from the experience.
Read MoreSoldiers Now Allowed To Tweet
The new rules authorize access to Facebook, Twitter, YouTube, and other social media Web sites from nonclassified government computers — as long as such activity doesn’t compromise operational security or involve prohibited activities or Web sites.
Read More